What is vSAN Trim/Unmap functionality?
This is an interesting feature of vSAN which came up in work recently. vSAN supports thin provisioning which lets you use as much capacity as currently needed where you can add more space in the future. One challenge to thin provisioning is that the VMDKs will not shrink when files within the guest O/S are deleted. An even bigger problem develops where many file systems will always direct new writes into free space rather than the old used space. Previous solutions to this involved manual intervention and storage vMotion to external storage or powering off an external machine. vSAN Trim/Unmap space reclamation solves this problem.
How does it work?
Modern guest O/S file systems have had the ability to reclaim no longer used space which are known as Trim/Unmap commands for the ATA and SCSI protocols. vSAN 6.7U1+ now has full awareness of Trim/Unmap commands sent from the guest O/S and can reclaim previously allocated storage as free space.
Benefits
- Faster repair means that blocks which have been reclaimed do not need to be rebalanced or remirrored in the event of a device failure
- Removal of dirty cache pages means that read cache can be freed up in the DRAM client cache as well as the hybrid vSAN SSD cache for use by other blocks. If removed from the write buffer then this reduces the number of blocks copied to the capacity tier.
Performance Impact
It does carry some performance impact as I/O must be processed to track pages which are no longer needed. The largest impact will be the UNMAPs issued against the capacity tier. vSAN 7U1 includes performance enhancements which help provide the fairness of UNMAPs in heavy write environments.
How is it enabled?
You can use either of the 2 CLI tools below.
- RVC
- PowerCLI
RVC
Enable = vsan.unmap_support <cluster> -e
Disable = vsan.unmap_support <cluster> -d
Powercycle the VMs
PowerCLI
Enable = Get-Cluster -name <cluster>|set-VsanClusterConfiguration–GuestTrimUnmap:$true
Disable = Get-Cluster -name <cluster>|set-VsanClusterConfiguration–GuestTrimUnmap:$false
Status = Get-Cluster -name <cluster>|get-VsanClusterConfiguration |ft GuestTrimUnmap
Powercycle the VMs
Powercycle command
You can run a command which will force a powercycle when the VM is next rebooted.
Get-Folder <foldername> | Get-VM | New-AdvancedSetting -Name vmx.reboot.PowerCycle -Value TRUE -Confirm:$false
Requirements
- A minimum of virtual machine hardware version 11 for Windows
- A minimum of virtual machine hardware version 13 for Linux.
- disk.scsiUnmapAllowed flag is not set to false. The default is an implied true. This setting can be used as a “kill switch” at the virtual machine level should you wish to disable this behaviour on a per VM basis and do not want to use in guest configuration to disable this behaviour. VMX changes require a reboot to take effect.
- The guest operating system must be able to identify the virtual disk as thin.
- After enabling at a cluster level, virtual machines must be power cycled
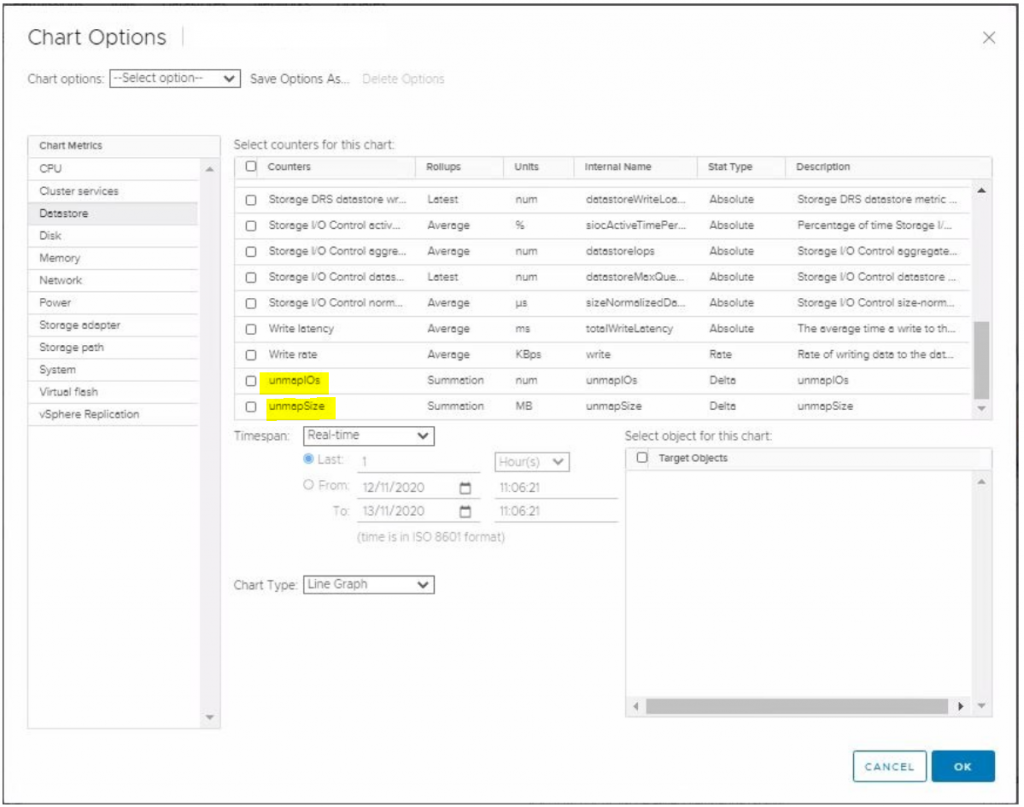
Monitoring TRIM/UNMAP
TRIM/UNMAP uses the following counters in the vSAN performance service for the hosts as seen in the figure below courtesy of VMware.
- UNMAP Throughput – The measure of UNMAP commands being processed by the disk groups of a host.
- Recovery UNMAP Throughput – The measure of throughput of UNMAP commands be synchronized as part of an object repair following a failure or absent object.
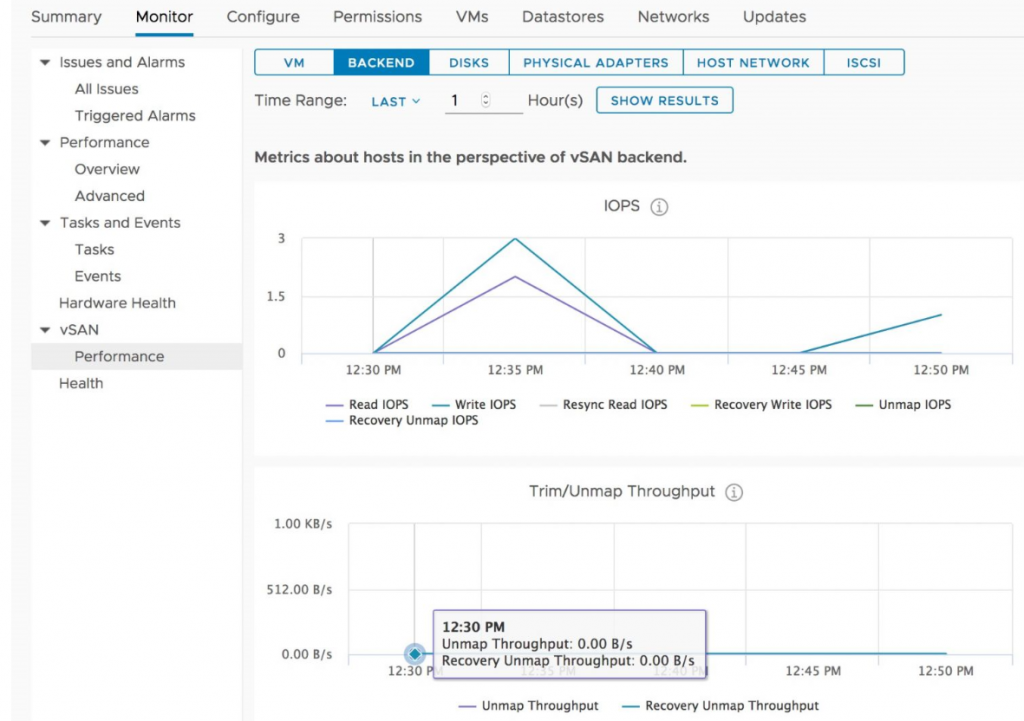
Using the advanced performance counters for a host will also show you the below counters