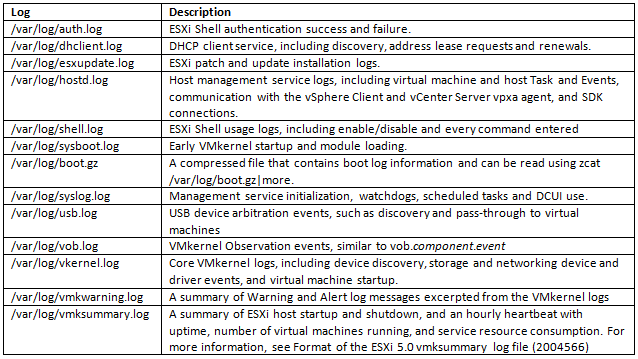
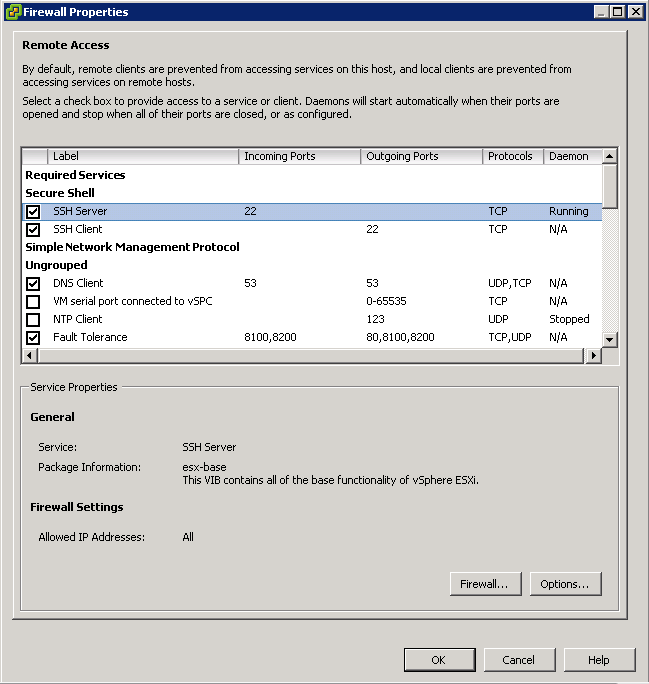
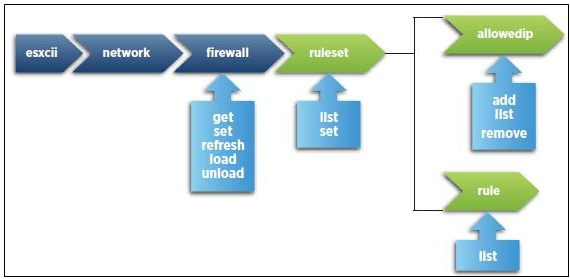
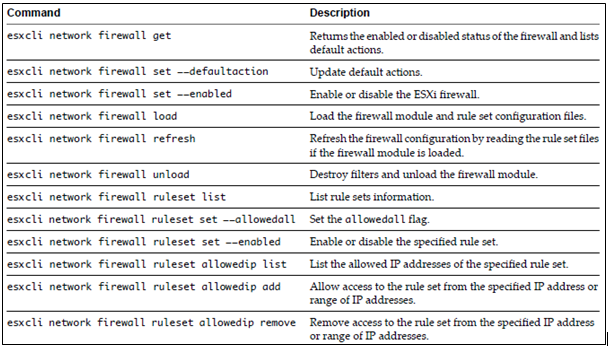
ESXi Password Information
By default, ESXi uses the pam_passwdqc.so plug-in to set the rules that users must observe when creating passwords and to check password strength.
The pam_passwdqc.so plug-in lets you determine the basic standards that all passwords must meet. By default, ESXi imposes no restrictions on the root password. However, when nonroot users attempt to change their passwords, the passwords they choose must meet the basic standards that pam_passwdqc.so sets.
Password Requirements
By default, ESXi enforces requirements for user passwords. When you create a password, include a mix of characters from four character classes: lowercase letters, uppercase letters, numbers, and special characters such as an underscore or dash.
Your user password must meet the following length requirements.
- Passwords containing characters from one or two character classes must be at least eight characters long.
- Passwords containing characters from three character classes must be at least seven characters long.
- Passwords containing characters from all four character classes must be at least six characters long.
NOTE: An uppercase character that begins a password does not count toward the number of character classes used. A number that ends a password does not count toward the number of character classes used.
You can also use a passphrase, which is a phrase consisting of at least three words, each of which is 8 to 40 characters long.
Example: Creating Acceptable Passwords
The following password candidates meet the requirements of ESXi.
- xQaTEhbU: Contains eight characters from two character classes.
- xQaT3pb: Contains seven characters from three character classes.
- xQaT3#: Contains six characters from four character classes.
The following password candidates do not meet the requirements of ESXi.
- Xqat3hb: Begins with an uppercase character, reducing the effective number of character classes to two.
Eight characters are required when you use only two character classes.
- xQaTEh2: Ends with a number, reducing the effective number of character classes to two.
Eight characters are required when you use only two character classes.
Configuring Password Complexity
To configure password complexity, you can change the default value of the following parameters.
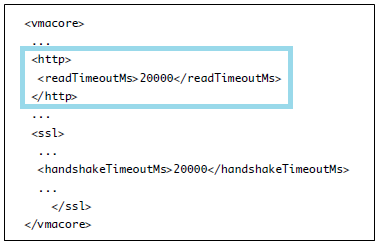
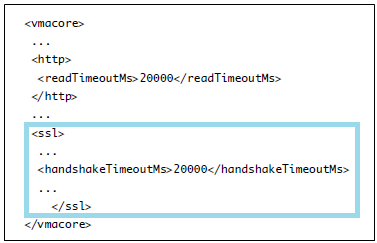
password requisite /lib/security/$ISA/pam_passwdqc.so retry=N min=N0,N1,N2,N3,N4
- retry is the number of times a user is prompted for a new password if the password candidate is not sufficiently strong.
- N0 is the number of characters required for a password that uses characters from only one character class. For example, the password contains only lowercase letters.
- N1 is the number of characters required for a password that uses characters from two character classes.
- N2 is used for passphrases. ESXi requires three words for a passphrase. Each word in the passphrase must be 8-40 characters long.
- N3 is the number of characters required for a password that uses characters from three character classes.
- N4 is the number of characters required for a password that uses characters from all four character classes.
- match is the number of characters allowed in a string that is reused from the old password. If the pam_passwdqc.so plug-in finds a reused string of this length or longer, it disqualifies the string from the strength test and uses only the remaining characters.
Setting any of these options to -1 directs the pam_passwdqc.so plug-in to ignore the requirement.
Setting any of these options to disabled directs the pam_passwdqc.so plug-in to disqualify passwords with the associated characteristic. The values used must be in descending order except for -1 and disabled.
Change Default Password Complexity for the pam_passwdqc.so Plug-In
Configure the pam_passwdqc.so plug-in to determine the basic standards all passwords must meet.
Procedure
- Log in to the ESXi Shell and acquire root privileges.
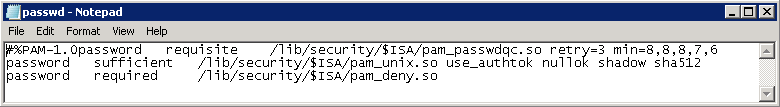
- Open the passwd file with a text editor or use WinSCP to download, modify and upload the passwd file
- For example, vi /etc/pam.d/passwd then type i which equals insert mode allowing input on the screen
- Edit the following line
password requisite /lib/security/$ISA/pam_passwdqc.so retry=N min=N0,N1,N2,N3,N4
- Type (ESC :wq to exit insert mode)
Example: Editing /etc/pam.d/passwd
password requisite /lib/security/$ISA/pam_passwdqc.so retry=3 min=12,9,8,7,6
With this setting in effect, the password requirements are:
- retry=3: A user is allowed 3 attempts to enter a sufficient password.
- N0=12: Passwords containing characters from one character class must be at least 12 characters long.
- N1=9: Passwords containing characters from two character classes must be at least nine characters long.
- N2=8: Passphrases must contain words that are each at least eight characters long.
- N3=7: Passwords containing characters from three character classes must be at least seven characters long.
- N4=6: Passwords containing characters from all four character classes must be at least six characters long.